The Kaspersky’s Global Research & Analysis Team has found a new malware attack using the DeepSeek name as a lure.
BrowserVenom is delivered alongside a real installer for DeepSeek, passing all browser traffic through a proxy controlled by attackers.
Kaspersky has detected the malware in South Africa, Brazil, Cuba, Mexico, India, Nepal, and Egypt.
Cybercriminals are leveraging the popularity of artificial intelligence platforms to peddle malware. Of late, cybercriminals have leaned on the popularity of AI platforms to disguise malware so that it spreads to more users.
The latest platform to be used as a lure is Chinese AI play DeepSeek. Kaspersky’s Global Research & Analysis Team has discovered a malicious campaign in which attackers are disguising BrowserVenom malware as a desktop application for PC. The attackers use Google Ads, and X posts to convince folks they are going to the official DeepSeek website, but in reality, it’s a ploy to install the malware.
The website looks very convincing and so does the installer which is labelled AI_launcher_1.21.exe. Once executed, a fake CAPTCHA screen is presented and if a user clicks the “I am not a robot” box, the next phase begins. The user is presented with the option to download either Ollama or LM Studio though which to run DeepSeek. The installer for either installer does run but at the same time a malicious payload is implanted on the PC.
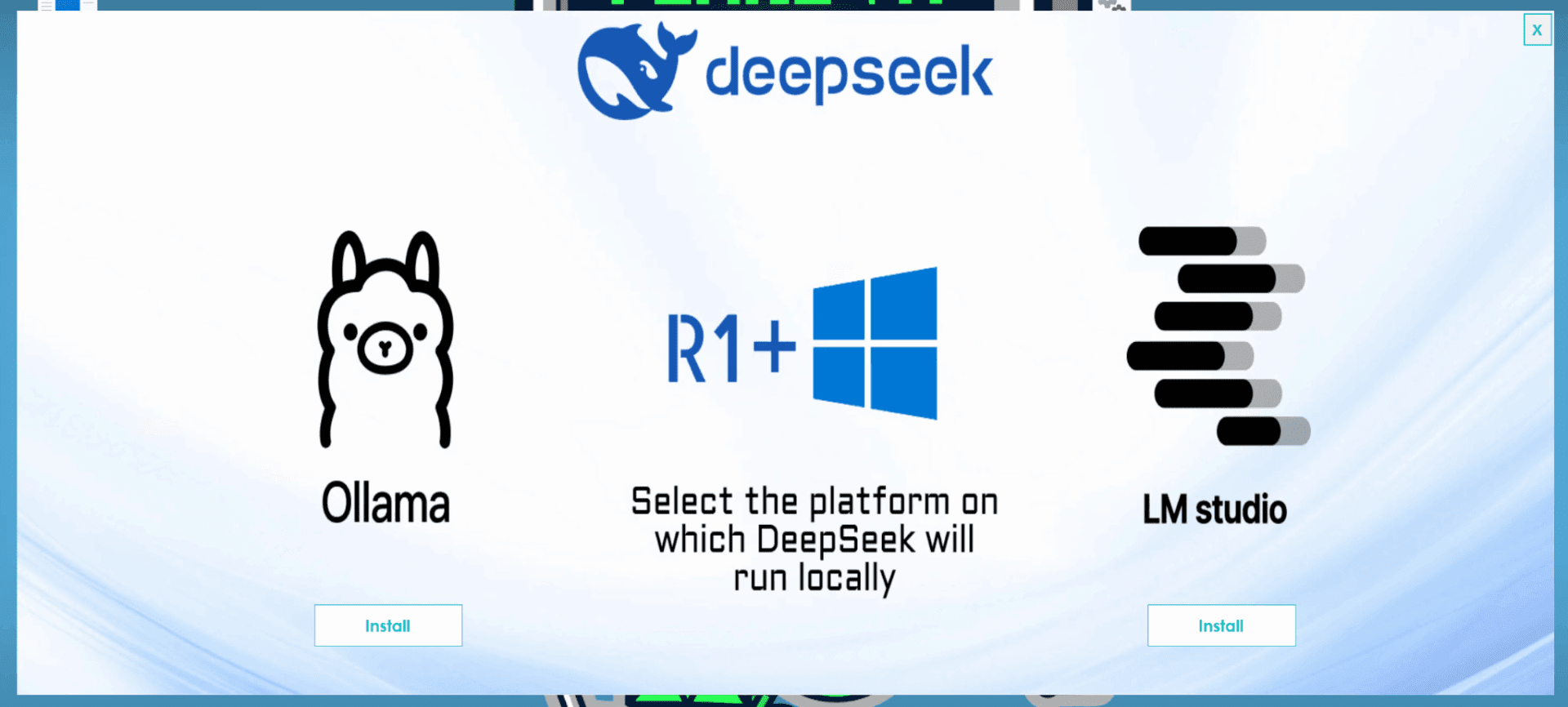
“We dubbed the next-stage implant BrowserVenom because it reconfigures all browsing instances to force traffic through a proxy controlled by the threat actors. This enables them to sniff sensitive data and monitor the victim’s browsing activity while decrypting their traffic,” Kaspersky GReAT explains.
Curiously, the malware seems to require that the user profile in use has administrator rights. If a check determines that the user doesn’t have administrator rights, it simply exits. If the user profile has administrator rights, a proxy server address is installed in all browsers through which traffic is routed.
This gives attackers access to everything that you access through your browser which may be a concern for any business that operates in the digital space. That is to say, all businesses.
“At the time of our research, we detected multiple infections in Brazil, Cuba, Mexico, India, Nepal, South Africa, and Egypt. The nature of the bait and the geographic distribution of attacks indicate that campaigns like this continue to pose a global threat to unsuspecting users,” say Kaspersky’s researchers.
The cybersecurity firm warns that users should be careful where they download software from in order to avoid malware such as BrowserVenom. For instance, this malware uses the website deepseek-platform.com, which isn’t related to the real DeepSeek in any way.
Furthermore, solutions offering free access to premium AI services are a major red flag and will likely lead to you downloading some like or worse than BrowserVenom.

