
Microsoft used its AI-powered Security Copilot to discover 20 previously unknown vulnerabilities in the GRUB2, U-Boot, and Barebox open-source bootloaders.
GRUB2 (GRand Unified Bootloader) is the default boot loader for most Linux distributions, including Ubuntu, while U-Boot and Barebox are commonly used in embedded and IoT devices.
Microsoft discovered eleven vulnerabilities in GRUB2, including integer and buffer overflows in filesystem parsers, command flaws, and a side-channel in cryptographic comparison.
Additionally, 9 buffer overflows in parsing SquashFS, EXT4, CramFS, JFFS2, and symlinks were discovered in U-Boot and Barebox, which require physical access to exploit.
The newly discovered flaws impact devices relying on UEFI Secure Boot, and if the right conditions are met, attackers can bypass security protections to execute arbitrary code on the device.
While exploiting these flaws would likely need local access to devices, previous bootkit attacks like BlackLotus achieved this through malware infections.
“While threat actors would likely require physical device access to exploit the U-boot or Barebox vulnerabilities, in the case of GRUB2, the vulnerabilities could further be exploited to bypass Secure Boot and install stealthy bootkits or potentially bypass other security mechanisms, such as BitLocker,” explains Microsoft.
“The implications of installing such bootkits are significant, as this can grant threat actors complete control over the device, allowing them to control the boot process and operating system, compromise additional devices on the network, and pursue other malicious activities.”
“Furthermore, it could result in persistent malware that remains intact even after an operating system reinstallation or a hard drive replacement.”
Below is a summary of the flaws Microsoft uncovered in GRUB2:
CVE-2024-56737 – Buffer overflow in HFS filesystem mounting due to unsafe strcpy on a non-null-terminated string
CVE-2024-56738 – Side-channel attack in cryptographic comparison function (grub_crypto_memcmp not constant-time)
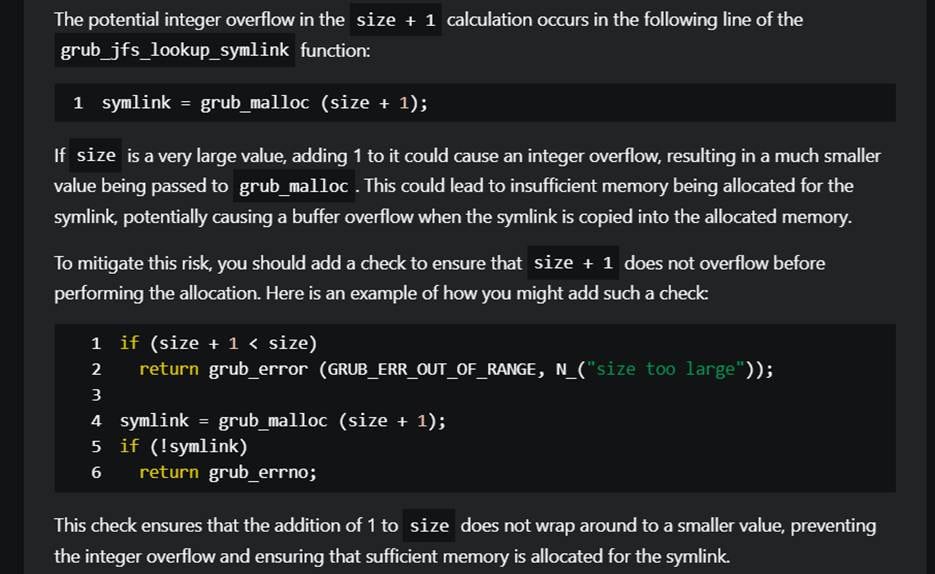
CVE-2025-0677 – Integer overflow in UFS symbolic link handling leads to buffer overflow
CVE-2025-0678 – Integer overflow in Squash4 file reading leads to buffer overflow
CVE-2025-0684 – Integer overflow in ReiserFS symbolic link handling leads to buffer overflow
CVE-2025-0685 – Integer overflow in JFS symbolic link handling leads to buffer overflow
CVE-2025-0686 – Integer overflow in RomFS symbolic link handling leads to buffer overflow
CVE-2025-0689 – Out-of-bounds read in UDF block processing
CVE-2025-0690 – Signed integer overflow and out-of-bounds write in read command (keyboard input handler)
CVE-2025-1118 – dump command allows arbitrary memory read (should be disabled in production)
CVE-2025-1125 – Integer overflow in HFS compressed file open causes buffer overflow
All of the above flaws are rated medium severity, except for CVE-2025-0678, which is rated “high” (CVSS v3.1 score: 7.8).
Microsoft says Security Copilot dramatically accelerated the vulnerability discovery process in a large and complex codebase, such as GRUB2, saving approximately 1 week of time that would be required for manual analysis.
Source: Microsoft
Not only did the AI tool identify the previously undiscovered flaws, but it also provided targeted mitigation recommendations that could provide pointers and accelerate the issuing of security patches, especially in open-source projects supported by volunteer contributors and small core teams.
Using the findings in the analysis, Microsoft says Security Copilot found similar bugs in projects utilizing shared code with GRUB2, such as U-boot and Barebox.
GRUB2, U-boot, and Barebox released security updates for the vulnerabilities in February 2025, so updating to the latest versions should mitigate the flaws.

Based on an analysis of 14M malicious actions, discover the top 10 MITRE ATT&CK techniques behind 93% of attacks and how to defend against them.
Read the Red Report 2025

